Retool Security: A Definitive Guide for Enterprise Users
When it comes to choosing a low-code tool for building enterprise apps, security remains a primary concern for decision-makers. Retool is one of the most widely adopted platforms in this space, used by companies like Amazon, DoorDash, and Brex to build internal admin panels, dashboards, and custom apps with minimal development overhead.
But for companies handling sensitive data – particularly in regulated industries – understanding how Retool handles security is a prerequisite to adoption.
This article will dive into Retool security architecture, including data access controls, infrastructure, compliance standards, and options for deploying securely within your own environment.
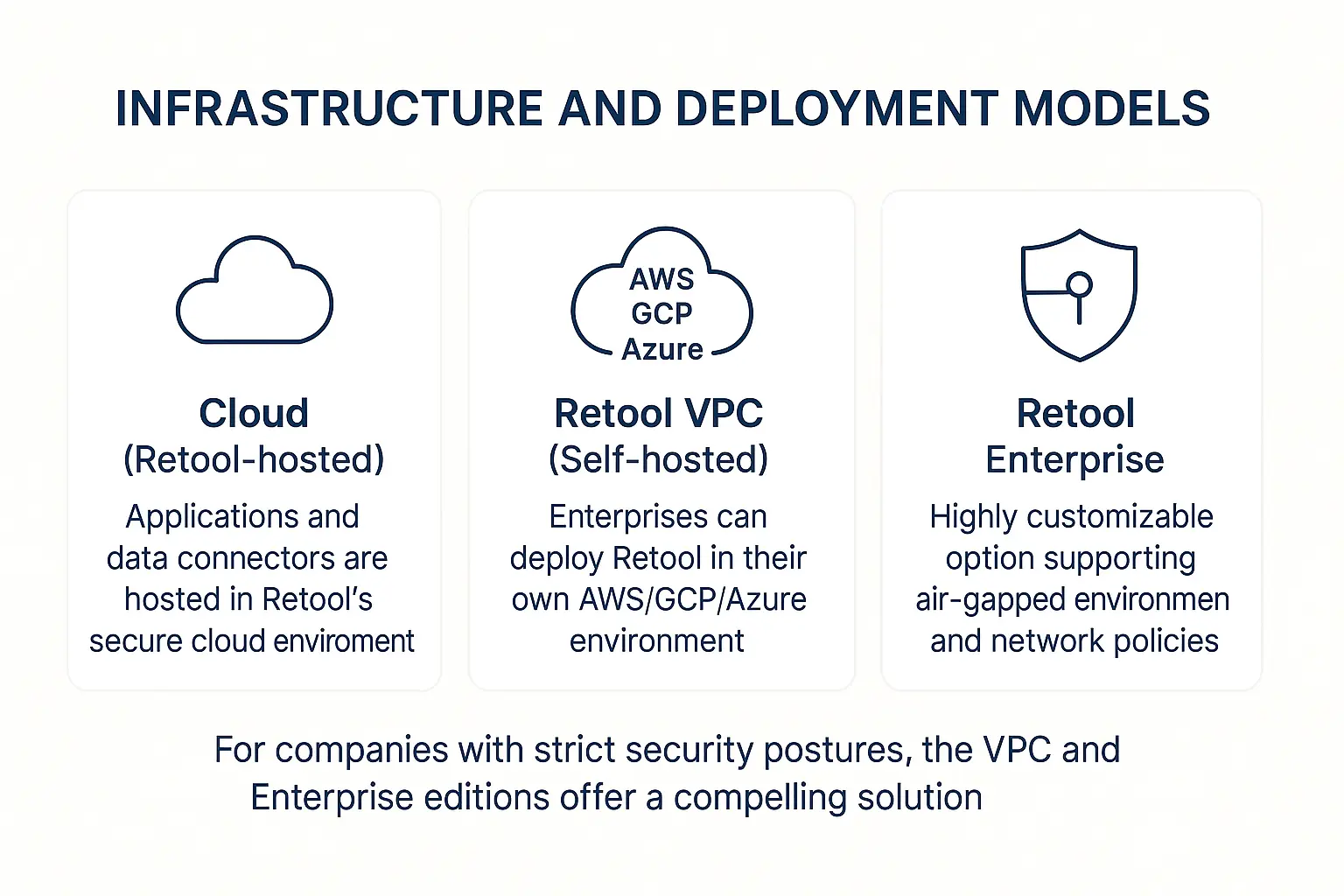
1. Infrastructure and deployment models
Retool offers multiple deployment options to meet varying security needs:
- Cloud (Retool-hosted): applications and data connectors are hosted in Retool’s secure cloud environment. This option will be best for teams that want minimal setup and maintenance.
- Retool VPC (Self-hosted): enterprises can deploy Retool in their own AWS/GCP/Azure environment. This grants complete control over data residency, network access, and integration with internal infrastructure.
- Retool Enterprise: a highly customizable option that supports air-gapped environments and granular network policies.
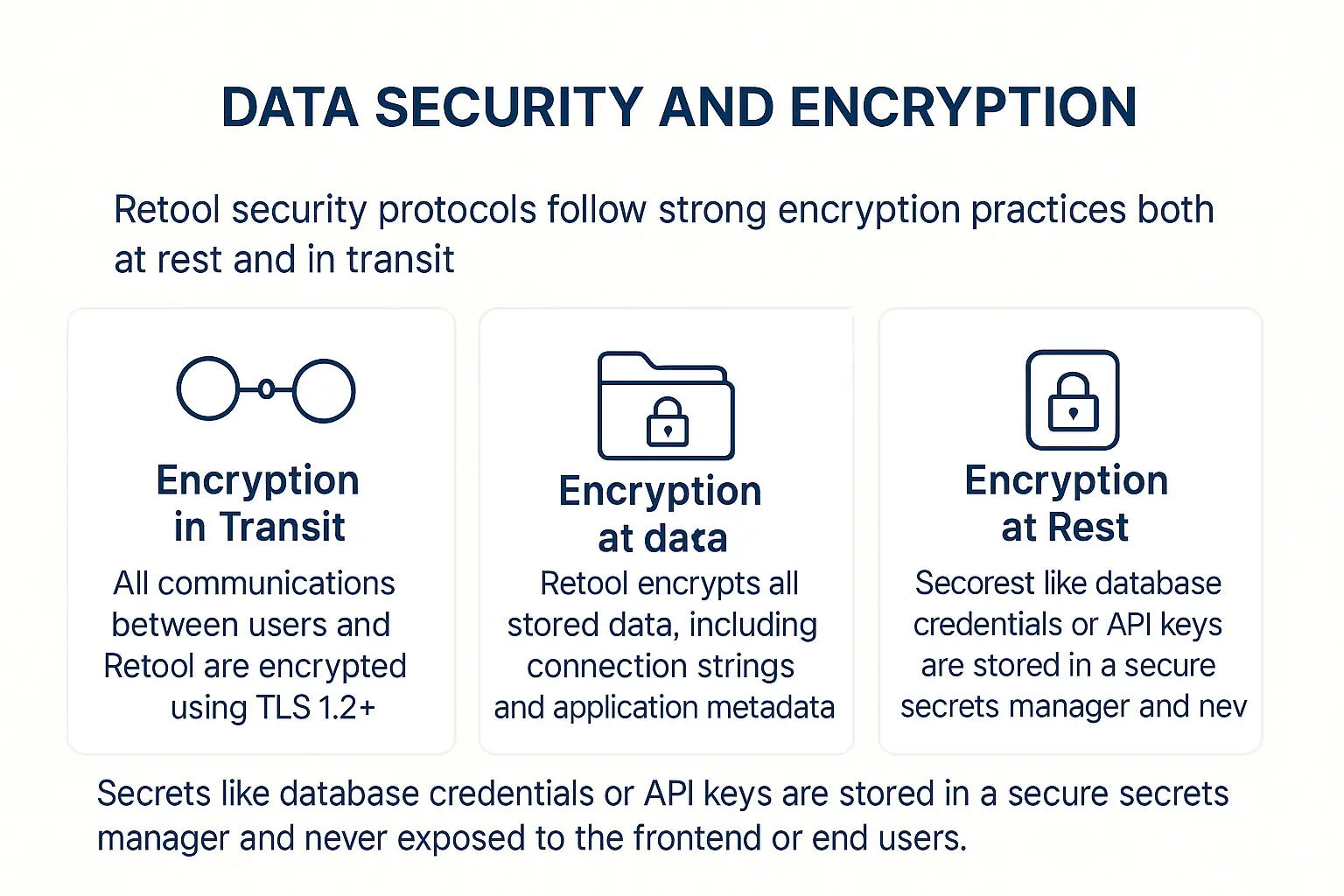
2. Data security and encryption
Retool security protocols follow strong encryption practices both at rest and in transit:
- Encryption in Transit – All communications between users and Retool are encrypted using TLS 1.2+.
- Encryption at Rest – Retool encrypts all stored data, including connection strings and application metadata, using AES-256 encryption.
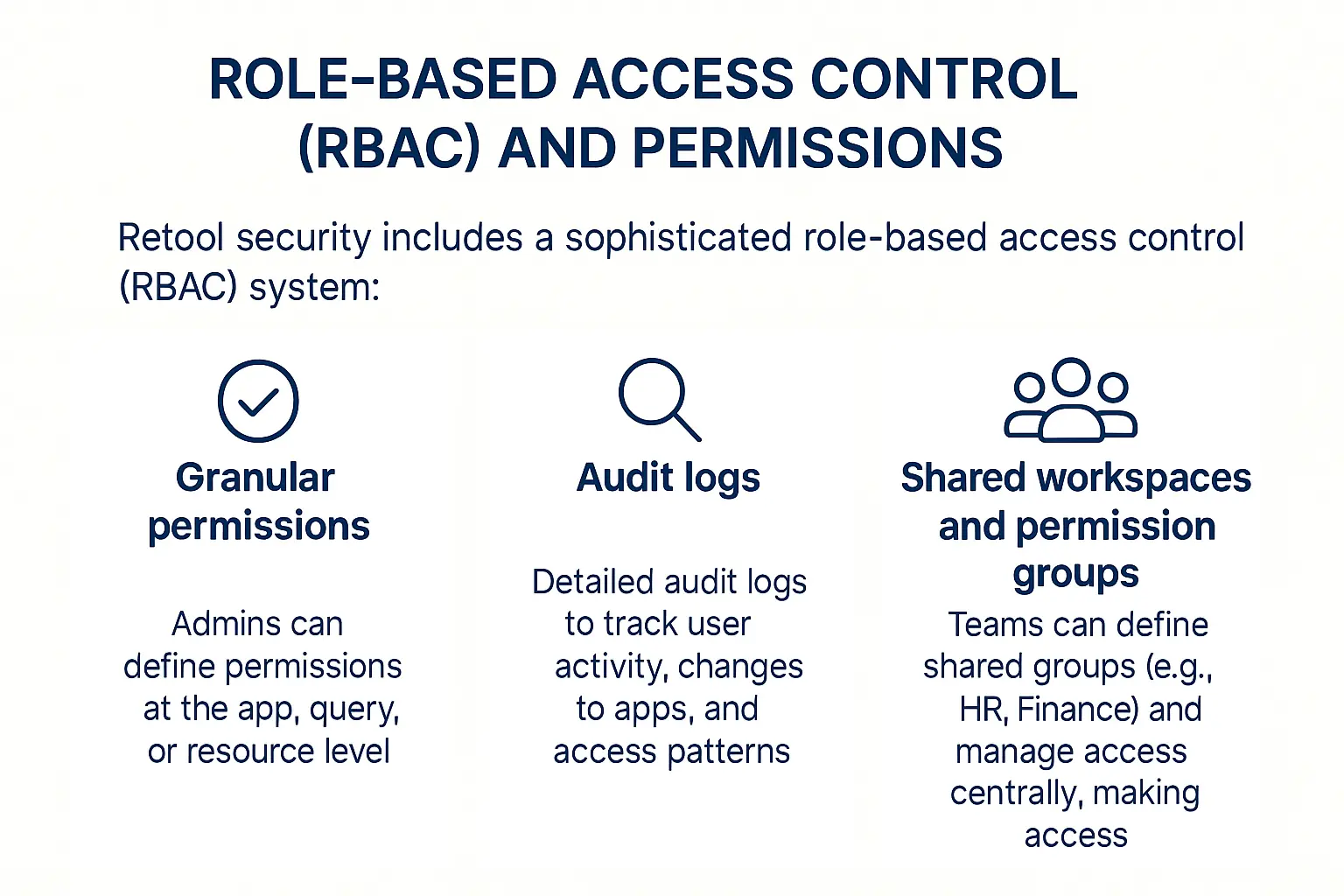
3. Role-based access control (RBAC) and permissions
Retool security includes a sophisticated role-based access control (RBAC) system:
- Granular permissions – Admins can define permissions at the app, query, or resource level. For instance, you can allow a user to view an app but prevent them from editing SQL queries or modifying data.
- Audit logs – Retool Enterprise provides detailed audit logs to track user activity, changes to apps, and access patterns for compliance and forensic analysis.
- Shared workspaces and permission groups – Teams can define shared groups (e.g., HR, Finance) and manage access centrally, making it easier to enforce the principle of least privilege.
4. Authentication and SSO integration
Retool low-code development platform supports enterprise-grade authentication mechanisms:
- Single Sign-On (SSO) – Integrates with Okta, Azure AD, Google Workspace, and any SAML or OpenID Connect provider.
- Multi-Factor Authentication (MFA) – Can be enforced across all users, adding another layer of protection against account compromise.
- SCIM Provisioning – Retool supports SCIM for automated user provisioning and de-provisioning, essential for managing employee lifecycle in large organizations.
5. Compliance and certifications
For enterprises operating in regulated industries, Retool’s compliance certifications are reassuring:
- SOC 2 Type II – Retool is SOC 2 Type II certified, demonstrating its adherence to stringent security, availability, and confidentiality standards.
- HIPAA Readiness – While Retool does not sign Business Associate Agreements (BAAs) by default, the self-hosted version enables teams to build HIPAA-compliant workflows.
- Data Residency – With VPC deployment, enterprises can ensure that all data remains in their region, meeting GDPR or other jurisdictional requirements.
6. Secure query execution and data flow
Security-conscious teams often worry about who has access to raw data or can modify backend logic. Retool security mitigates this risk by:
- Running backend queries on secure servers (never in the user’s browser).
- Providing read-only environments for production apps.
- Offering parameterized queries and environment-based secrets to prevent injection attacks and accidental data leaks.
7. Change management and versioning
Retool offers Git-based version control for enterprise customers:
- Developers can push and pull app versions via Git.
- App changes are tracked and auditable, which is essential for teams that require change control procedures and CI/CD integration.
8. Security for embedded apps
When embedding Retool apps in internal tools or customer portals, security boundaries remain intact:
- You can restrict access via signed JWTs and token-based authentication.
- Retool supports row-level security based on user identity, ensuring users only see the data they’re authorized to access.
UI Bakery: enterprise-grade security by design
While Retool provides a robust security model, UI Bakery is another enterprise-ready low-code platform that places security at the core of its architecture. Here is an overview of key security aspects UI Bakery follows:
- Full on-prem deployment – Just like Retool, UI Bakery can be deployed entirely within your own infrastructure (self-hosted), ensuring zero data leaves your environment.
- Granular permission management – UI Bakery also supports team-based access control, with permission groups and audit trails.
- SOC 2 compliance & GDPR readiness – UI Bakery follows latest industry practices and is compliant with key security and data protection standards.
- Custom domain and white-labeling – Enterprises can fully control the domain, branding, and authentication flow.
- Custom authentication logic – For teams requiring SSO, 2FA, or integration with custom auth providers, UI Bakery offers full flexibility in authentication flow design.
UI Bakery stands as a strong, privacy-conscious Retool security alternative that doesn’t compromise on customizability or control.
Wrapping up
Retool has invested heavily in securing its platform, offering both the flexibility and compliance features needed by enterprise teams. From RBAC and audit trails to VPC deployments and encryption at every level, it’s designed for teams that can’t afford to compromise on data protection.
That said, platforms like UI Bakery are pushing the envelope by offering similar security features along with more customizable deployment options, making them worthy contenders in the enterprise low-code space.
Security is not a feature – it's a foundation, especially when it comes to enterprise development. Whether you're building internal admin tools or customer-facing apps, make sure your platform respects your data as much as you do.






