CRUD Permissions: Managing Access and Security with UI Bakery
Managing access control and user permissions is a cornerstone of application security and user management. Whether you're developing a small internal tool or a large-scale application, setting up proper permissions for CRUD operations ensures data integrity and protects sensitive information from unauthorized access. In this blog post, we'll delve into the fundamentals of CRUD permissions, explore how to implement these permissions effectively, and show how UI Bakery's built-in roles and permissions functionality can simplify the process.
What are CRUD permissions?

At the heart of any software application, CRUD operations define the basic interactions users have with data:
- Create: Adding new data (e.g., a new user or product).
- Read: Viewing existing data (e.g., fetching product details).
- Update: Modifying existing data (e.g., editing a user's profile).
- Delete: Removing data (e.g., deleting a record or an account).
Managing who has access to perform each of these actions is essential for maintaining the integrity and security of an application. For instance, while administrators might have full access to CRUD operations, regular users might only have the ability to create and read records, but not update or delete them.
CRUD permissions act as a gatekeeper, controlling which roles within an application are granted the authority to execute specific actions on various resources.
Why are CRUD permissions important?
- Data Security: By controlling who can view, modify, or delete data, CRUD permissions help prevent unauthorized access and potential breaches. Sensitive data must be accessible only by those who are authorized to handle it.
- Minimizing Errors: Giving too many people the ability to modify or delete data increases the risk of accidental changes. By restricting CRUD operations to certain roles, you reduce human errors that could lead to data loss or inconsistency.
- Regulatory Compliance: Many industries require strict access controls to comply with regulations such as GDPR, HIPAA, and PCI-DSS. CRUD permissions help ensure compliance by limiting access to sensitive information based on a user's role.
- Improving User Experience: Well-implemented CRUD permissions enhance the user experience by ensuring users only see the options they are allowed to interact with. This prevents confusion and ensures a streamlined interface.
Implementing CRUD permissions in applications
When building an application, implementing CRUD permissions usually follows a role-based access control (RBAC) model. In this model, users are assigned roles, and roles are associated with specific permissions.
Role-based access control (RBAC)
In a typical RBAC model:
- Roles define a set of permissions (e.g., Admin, Editor, Viewer).
- Permissions define what actions a role can take on a given resource (e.g., an Admin can perform all CRUD actions, while a Viewer can only read data).
- Users are assigned one or more roles, which determine their access rights.
Example:
- An Admin role might have full access to all CRUD operations for every resource in the system.
- A User role might have permission to create and read records but not update or delete them.
- A Guest role might only be able to view certain public data, with no permissions to create, update, or delete anything.
This hierarchical approach is scalable, making it easier to manage permissions as your application grows. It’s crucial, however, to implement it efficiently, ensuring there are no loopholes that could lead to unauthorized access.
Challenges in managing CRUD permissions
Managing CRUD permissions, especially in complex applications, can pose several challenges:
- Complexity in Rules: As the application grows, so do the number of resources and roles, which can lead to a complicated and hard-to-manage set of permissions.
- Permission Overlaps: When a user has multiple roles with conflicting permissions, it becomes challenging to resolve which permission should take precedence.
- Granularity: Finding the right balance between general roles and specific permissions can be difficult. Too broad permissions can open up security vulnerabilities, while too granular permissions can overwhelm the system with complexity.
- Auditing and Maintenance: Keeping track of who has access to what data and ensuring that permissions are up-to-date requires continuous auditing, especially in fast-paced development environments.
To address these challenges, it’s essential to have a clear and intuitive permissions management system. This is where UI Bakery can help.
How UI Bakery’s roles and permissions functionality simplifies CRUD management
UI Bakery offers a robust set of features that help developers easily manage CRUD permissions, ensuring secure and efficient role-based access control. With UI Bakery, you can visually define and manage roles and permissions without the complexity of coding access control from scratch.
Key features of UI Bakery’s roles and permissions system
- Visual Role Management: UI Bakery provides an intuitive, visual interface for defining roles and assigning CRUD permissions to different resources. Instead of manually writing permission rules in code, you can manage everything within the platform, significantly reducing development time.
- Granular Permissions: You can assign permissions for each individual CRUD operation (Create, Read, Update, Delete) on a per-resource basis. This means you can precisely control what each role is allowed to do, ensuring that users only have access to the necessary parts of the application.
- Flexible Roles: UI Bakery supports the creation of flexible roles that can be assigned to users. Whether your application requires standard roles like Admin and User or more complex role structures with unique permissions, you can easily configure them within UI Bakery’s interface.
- Easy Updates and Maintenance: When your application evolves, and you need to change permissions, UI Bakery makes it easy to modify roles without touching code. Updates can be made on the fly, ensuring that your access control policies remain up to date.
- User-friendly Interface: The drag-and-drop approach UI Bakery uses makes assigning permissions to roles a straightforward process. You don't need to be an expert in backend development or access control frameworks to manage permissions in your app.
- Pre-Built Templates: UI Bakery provides pre-built templates for common roles and permissions setups, helping you quickly implement standard access control models. This is particularly useful for developers looking to fast-track their development process without sacrificing security.
- API Integration: For teams with more advanced use cases, UI Bakery allows for seamless integration with external APIs. This means you can use UI Bakery’s interface to manage permissions for data and operations that reside outside of UI Bakery itself.
Example: Setting up CRUD permissions with UI Bakery
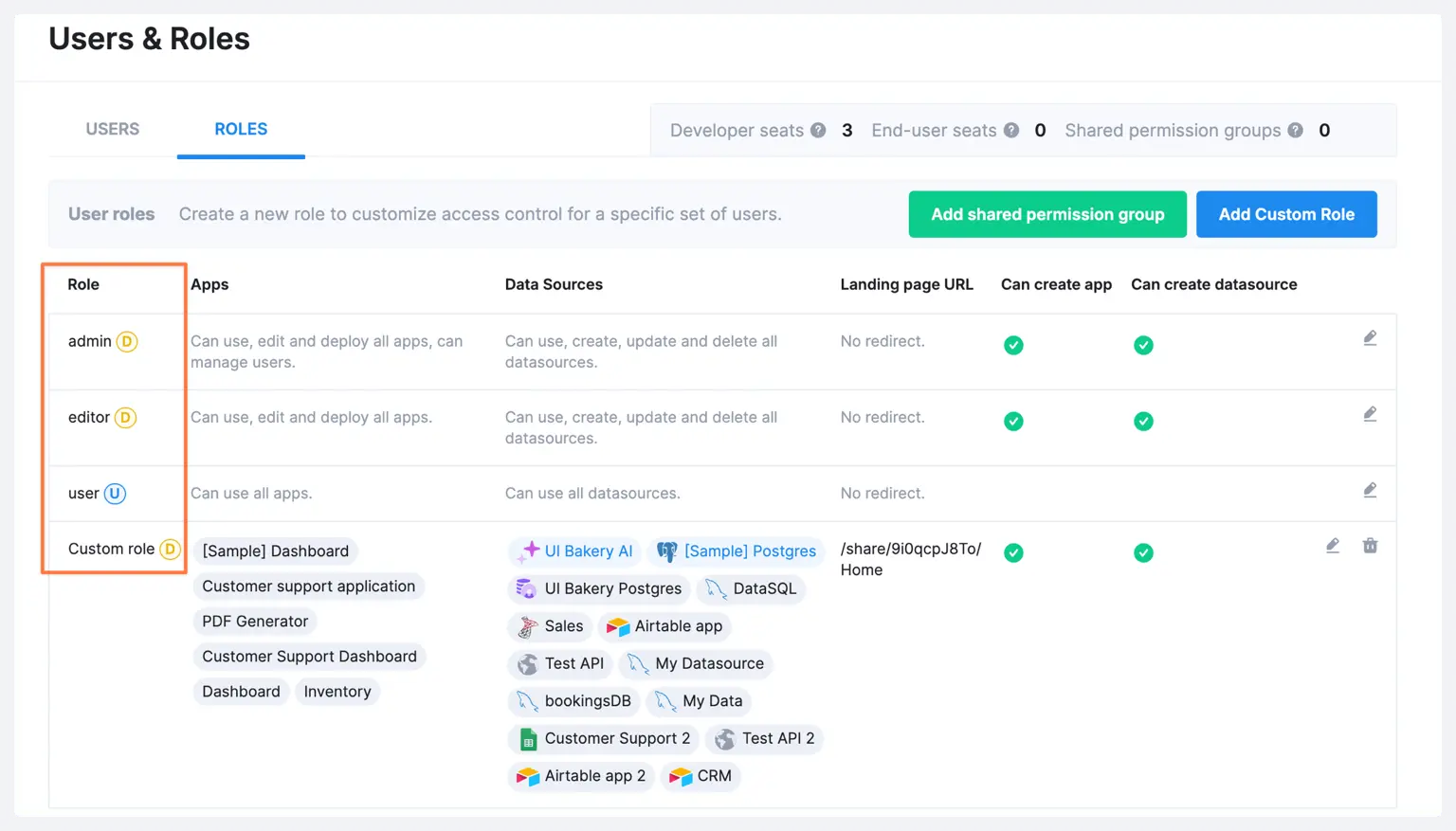
Let’s walk through a simple example to illustrate how you can manage CRUD permissions using UI Bakery.
Imagine you're building an employee management system with three types of users: Admins, Editors, and Users.
- Create Roles: In UI Bakery, you would start by creating these three roles: Admin, Editor, and User.
- Assign CRUD Permissions:some text
- The Admin role gets full access to CRUD operations on all resources (employees, departments, etc.).
- The Editor role can create, read, and update employee records but cannot delete them.
- The User role can only view their own data (read-only permission).
- Assign Roles to Users: Once the roles are set up, you can assign these roles to users in your application. As users log in, UI Bakery ensures that they only see the actions they are permitted to perform.
This simple yet effective approach reduces the potential for error, increases security, and ensures a consistent user experience.
Conclusion
CRUD permissions are a fundamental aspect of application security, ensuring that data is accessed and manipulated only by authorized users. By implementing a robust permissions system using UI Bakery, developers can significantly simplify the management of roles and access control in their applications.
UI Bakery’s roles and permissions functionality provides an intuitive and flexible solution for managing CRUD operations, allowing you to focus more on building your application and less on the complexities of access control. Whether you’re working with a small team or managing a large-scale enterprise application, UI Bakery helps ensure that your application’s security and user permissions are always under control.
Start using UI Bakery today to manage your CRUD permissions with ease. You can explore more in-depth details in UI Bakery’s documentation and see how it can help your project achieve better role-based access control.